Overview of the Trojan go protocol
The Trojan Go protocol is a powerful tool used by cybersecurity professionals to conduct penetration tests and assess a network's vulnerabilities. It is designed to mimic the behavior of a Trojan horse, infiltrating a system undetected to provide valuable information about its security weaknesses. This protocol operates by allowing the attacker to manipulate the target network from within, simulating the actions of a real attacker.
Importance of understanding how it works
For businesses and organizations, understanding how the Trojan Go protocol works is crucial for ensuring the security of their networks. By familiarizing themselves with this protocol, they can adopt necessary defenses to protect against potential attacks. Additionally, knowledge of the Trojan Go protocol can help organizations identify vulnerabilities, develop effective countermeasures, and train their employees to recognize and respond to potential threats.
By understanding the inner workings of the Trojan Go protocol, businesses can proactively strengthen their network security and prevent unauthorized access to sensitive information. It allows them to stay one step ahead of cybercriminals and minimize the risk of data breaches or other cybersecurity incidents. Therefore, investing the time and resources to understand how the Trojan Go protocol works is a vital aspect of maintaining a robust cybersecurity posture.
Conclusion
In conclusion, the Trojan Go protocol is an essential tool in the field of cybersecurity. By understanding its mechanisms and functionalities, businesses can enhance their network security, protect their sensitive data, and mitigate the risks associated with cyber threats. It is crucial for organizations to invest in comprehensive cybersecurity measures, including understanding the Trojan Go protocol, to stay ahead of potential threats and ensure the trust and confidence of their customers.
What is a Trojan go protocol?
Definition and explanation of the Trojan go protocol
The Trojan Go protocol is a powerful tool used in the realm of cybersecurity. It is designed to emulate the behavior of a Trojan horse, infiltrating a system undetected to gather valuable information about its vulnerabilities. This protocol allows cybersecurity professionals to conduct penetration tests, assess a network's security, and identify potential weaknesses.
At its core, the Trojan Go protocol operates by enabling attackers to manipulate the target network from within, mimicking the actions of a real attacker. This protocol is typically employed by ethical hackers and cybersecurity experts to evaluate the effectiveness of an organization's security measures and identify areas that need improvement.
Key characteristics and functions
The Trojan Go protocol possesses several key characteristics and functions that make it an invaluable tool in the field of cybersecurity. These include:
-
Stealth and Infiltration: The Trojan Go protocol is designed to infiltrate a system undetected, mimicking the behavior of an actual Trojan horse. This allows cybersecurity professionals to assess the system's vulnerabilities without alerting potential attackers.
-
Information Gathering: Once inside the target network, the Trojan Go protocol collects valuable information about the system's strengths and weaknesses. This data aids in identifying potential security vulnerabilities and developing appropriate countermeasures.
-
Replication and Control: Similar to a Trojan horse, the Trojan Go protocol can replicate itself and gain control over various aspects of the target network. This allows cybersecurity professionals to simulate the actions of an attacker and assess the network's response to different attack scenarios.
-
Realistic Assessment: By utilizing the Trojan Go protocol, organizations can gain a realistic understanding of their network's security posture. This assessment helps them identify potential shortcomings, implement necessary defenses, and train their employees to recognize and respond effectively to cybersecurity threats.
In conclusion, the Trojan Go protocol is a powerful tool in the world of cybersecurity. It allows organizations to evaluate their network's vulnerabilities, develop effective countermeasures, and stay one step ahead of potential cyber threats. Understanding the mechanisms and functionalities of the Trojan Go protocol is crucial for maintaining a strong cybersecurity posture and safeguarding sensitive data and information.
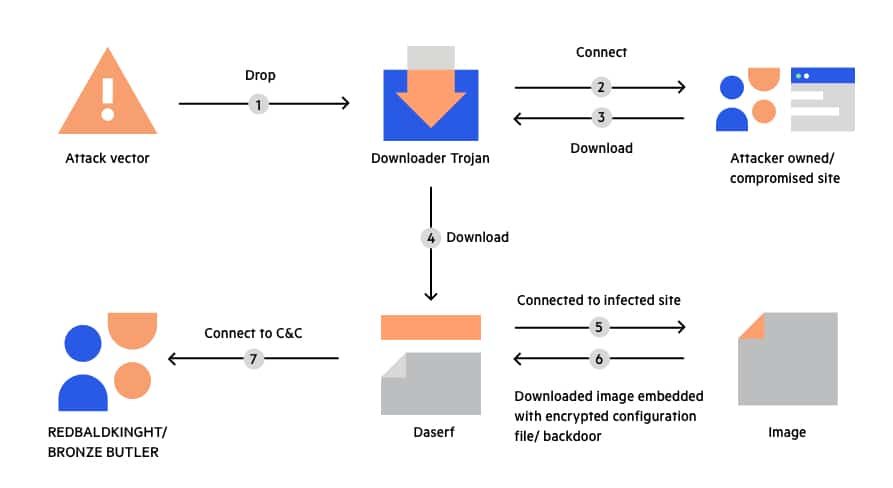
History of the Trojan go protocol
Origins and development of the Trojan go protocol
The Trojan Go protocol has a fascinating history that dates back to the early days of cybersecurity. It was first developed as a tool to emulate the behavior of a Trojan horse, a concept inspired by the legendary ancient Greek story. The original goal was to create a protocol that could infiltrate a system undetected and gather valuable information about its vulnerabilities.
Over time, the Trojan Go protocol evolved and underwent significant advancements. Ethical hackers and cybersecurity experts recognized its potential as a powerful tool for conducting penetration tests and assessing network security. This led to further development and refinement of the protocol, making it more effective and versatile in identifying potential weaknesses within a system.
Evolution and advancements over time
As technology progressed, so did the Trojan Go protocol. With each passing year, new techniques and features were introduced to enhance its capabilities and ensure its effectiveness in the ever-changing landscape of cybersecurity.
One significant advancement in the Trojan Go protocol was the incorporation of stealth and infiltration capabilities. This allowed the protocol to mimic the behavior of a real attacker, entering the target system undetected. By doing so, cybersecurity professionals could accurately assess vulnerabilities without alerting potential attackers or disrupting normal system operations.
Another key advancement was the ability of the Trojan Go protocol to replicate itself and gain control over various aspects of the target network. This functionality enabled a realistic simulation of an attacker's actions, providing valuable insights into the network's security response and helping organizations develop appropriate countermeasures.
Overall, the Trojan Go protocol has evolved into a highly sophisticated and essential tool in the field of cybersecurity. It empowers organizations to assess their network's vulnerabilities, proactively address weaknesses, and enhance their overall security posture. By staying abreast of the protocol's history, origins, and advancements, cybersecurity professionals can leverage its power to safeguard sensitive data and information effectively.

Working Principles of the Trojan go Protocol
Basic Principles and Components
The Trojan go protocol is a highly sophisticated cybersecurity tool used by ethical hackers and organizations to assess network vulnerabilities. At its core, the protocol operates based on two fundamental principles: stealth and information gathering.
Stealth is achieved through the protocol's ability to mimic the behavior of a real attacker. By blending in with normal network traffic and avoiding detection, it can effectively infiltrate target systems without raising any alarms. This allows cybersecurity professionals to accurately assess the system's vulnerabilities without tipping off potential attackers.
The Trojan go protocol consists of several components that work together seamlessly. These components include the client, server, and communication channels. The client component is responsible for initiating the connection and executing the protocol's functions, while the server component receives and processes the data transmitted by the client.
Data Transmission and Encryption
To ensure the security and integrity of the data transmitted, the Trojan go protocol employs robust encryption techniques. It uses advanced encryption algorithms to protect the sensitive information being gathered from the target system. This encryption ensures that even if the communication is intercepted, the data remains unreadable and inaccessible to unauthorized individuals.
Furthermore, the protocol utilizes secure communication channels to transmit the encrypted data. These channels are resistant to interception and tampering, providing an additional layer of protection. The data is carefully packaged and transmitted through these channels to the server component, where it is decrypted and analyzed.
By combining stealthy infiltration, sophisticated encryption, and secure communication channels, the Trojan go protocol is able to effectively gather valuable information about a system's vulnerabilities. It empowers organizations to proactively address weaknesses and enhance their overall cybersecurity posture. Understanding the basic principles and components, as well as the data transmission and encryption mechanisms, allows cybersecurity professionals to effectively utilize the Trojan go protocol to safeguard sensitive data and information.

Trojan go protocol in action
Implementation and usage scenarios
The Trojan go protocol is a powerful cybersecurity tool used by ethical hackers and organizations to assess the vulnerabilities of a network. It operates based on two key principles: stealth and information gathering. By mimicking the behavior of a real attacker, the protocol can infiltrate target systems without raising any alarms. This allows cybersecurity professionals to accurately assess the system's weaknesses and address them proactively.
The protocol consists of several components, including the client, server, and communication channels. The client component initiates the connection and executes the protocol's functions, while the server receives and processes the transmitted data. This seamless collaboration ensures efficient and effective information gathering.
Examples of popular applications and services
The Trojan go protocol has found applications in various industries and use cases. For instance, it is commonly used by organizations to test the security of their own systems and identify vulnerabilities before potential attackers can exploit them. Ethical hackers also utilize the protocol to assess the weaknesses of their clients' networks and provide recommendations for improvement.
Many cybersecurity consulting firms and penetration testing teams offer services that utilize the Trojan go protocol. They conduct thorough assessments of clients' systems, identify vulnerabilities, and offer tailored solutions to enhance security. Additionally, government agencies and law enforcement organizations use the protocol to investigate potential cyber threats and gather valuable intelligence.
In conclusion, the Trojan go protocol is an invaluable tool in the field of cybersecurity. Its stealthy infiltration, robust encryption techniques, and secure communication channels make it highly effective in gathering valuable information about a system's vulnerabilities. By utilizing this protocol, organizations can strengthen their cybersecurity posture and safeguard sensitive data and information.







