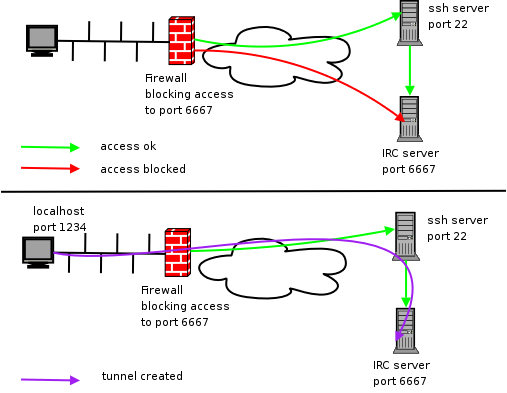
Get instant secure access with Dropbear SSH config-free servers in Australia: Experience blazing-fast Australian connectivity, zero configuration setup, robust encrypted tunnels, remote command-line access, and reliable local performance for secure file transfers and remote administration.
Share our website on social media
- 10GB/s
- Free account SSH Dropbear every 4 days
- Location : Australia
- City : Canberra
- SSL/TLS support
No Torrent
Accounts on server : 161
Server ID : A85
Advanced Server Configuration
Setting Up the dropbear ssh server
To configure the Dropbear SSH server for optimal performance and security on Australia networks, ensure that your server’s hardware meets the required specifications. Use the dropbear command-line utility to initiate the server with customized options. For instance:
dropbear -p 2222 -W 65536This command starts the Dropbear SSH server on port 2222 with a maximum window size of 65536 bytes, which accommodates high-latency networks commonly found in expansive regions such as Australia.
Key Authentication and User Management
Implement SSH key authentication to enhance security. Generate an SSH key pair via the following command:
ssh-keygen -t rsa -b 4096Place the public key in ~/.ssh/authorized_keys on the server. Use the -s option to specify a different authorized keys file if necessary.
Custom Protocol Implementation
SSHv2 Features
Leverage SSHv2 features in Dropbear to enhance protocol robustness. Apply the compression and MAC algorithms for improved performance:
dropbear -c none -m hmac-sha2-256This configuration disables compression to reduce CPU load and uses a strong MAC algorithm for data integrity.
Load Balancing and Failover Setup
Configuring Load Balancing
Integrate Dropbear with a load balancer to handle multiple SSH connections efficiently across servers. Use HAProxy as a reverse proxy:
frontend ssh-in
bind :22
default_backend ssh-backend
backend ssh-backend
balance roundrobin
server server1 192.168.1.1:22 check
server server2 192.168.1.2:22 check
Failover Techniques
Implement failover by configuring multiple servers in the backend. Ensure all servers have identical Dropbear configurations to maintain session consistency in failover events.
Advanced Security Hardening
Mitigating SSH Dropbear Vulnerabilities
Regularly update Dropbear to the latest version to mitigate known vulnerabilities. Enhance security using rate limiting and IP whitelisting. For instance, employ iptables for rate limiting:
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -m recent --setSecurity Best Practices
- Disable root login by setting
PermitRootLogin noin the Dropbear configuration file. - Restrict user logins to specific IP ranges.
Network Optimization for Australia Infrastructure
Australia’s vast geography necessitates network optimization. Use TCP Keep-Alive to maintain active connections:
dropbear -K 60 -I 600This setting sends a keep-alive packet every 60 seconds, with an idle timeout of 600 seconds.
Monitoring and Logging Systems
Setting Up Enhanced Logging
Enable verbose logging for monitoring user activities and system status. Redirect logs to a centralized syslog server:
dropbear -v | logger -t dropbearMonitoring Tools
- Use Nagios or Zabbix to monitor server availability and performance metrics.
- Implement log rotation to manage disk space efficiently.
Automation and Scripting Solutions
Scripting for Configuration Management
Automate configuration deployment using shell scripts or tools like Ansible. A sample script for deploying Dropbear configurations could be:
#!/bin/bash
CONFIG_FILE="/etc/dropbear/dropbear_config"
scp $CONFIG_FILE user@remote:/etc/dropbear/
ssh user@remote 'systemctl restart dropbear'
Cron Jobs for Maintenance
Schedule regular maintenance and updates using cron jobs. For example, automate the update of Dropbear:
0 2 * 1 apt-get update && apt-get upgrade -y dropbearThis job runs weekly, ensuring the server remains up to date with the latest security patches.
Latest 10 Post about SSH Dropbear on Blog