where cyber threats are becoming more sophisticated, ensuring internet security is crucial. With the advancement of technology, new protocols are constantly being developed to enhance security measures. One such protocol is VLESS free, which is an extension of V2Ray. In this blog, we will provide an overview of V2Ray and VLESS protocol, emphasizing the importance of internet security and privacy.
Overview of V2Ray and VLESS protocol
V2Ray: V2Ray vless is an open-source network proxy tool designed to improve internet privacy, security, and bypass censorship. It operates by allowing users to create customizable routing rules to redirect their internet traffic through various protocols, including TCP, mKCP, WebSocket, and more. V2Ray ensures secure and efficient communication between the client and server by utilizing encryption and obfuscation techniques.
VLESS: VLESS is an encryption protocol that builds upon the features of V2Ray, further enhancing security and privacy. It utilizes the Transport Layer Security (TLS) protocol to establish a secure and encrypted connection between client and server. VLESS supports various cipher suites, including AES, ChaCha20, and more, to ensure data confidentiality. Additionally, it offers obfuscation techniques to disguise network traffic, making it more challenging for adversaries to detect and block.
Importance of internet security and privacy
With the increasing prevalence of cyber attacks, protecting sensitive information has become paramount. Internet security and privacy are crucial for individuals and organizations alike. Malicious actors can exploit vulnerabilities to steal personal and financial data, disrupt services, or spy on users.
By adopting robust security measures like V2Ray with the VLESS protocol, users can enjoy enhanced protection against these threats. The encryption and obfuscation techniques employed by V2Ray and VLESS make it harder for hackers and surveillance agencies to intercept or decipher the transmitted data. This ensures a higher level of confidentiality, integrity, and authenticity.
Furthermore, VLESS provides users with the ability to bypass censorship and access restricted content by disguising their network traffic. This is especially important for individuals living in countries with strict internet regulations.
In conclusion, the V2Ray VLESS protocol offers an effective solution for boosting internet security and privacy. By implementing this protocol, individuals and organizations can safeguard their data and communications from unauthorized access and surveillance. It is crucial to prioritize internet security and take proactive measures to protect sensitive information in today's interconnected world.

Understanding VLESS Protocol
Explanation of VLESS protocol and its advantages
VLESS protocol is an extension of the popular V2Ray protocol, specifically designed to enhance internet security and privacy. By incorporating advanced encryption and obfuscation techniques, VLESS provides users with a reliable and secure connection.
Enhanced Security: VLESS utilizes the Transport Layer Security (TLS) protocol to establish a secure and encrypted connection between the client and server. This ensures that all data transmitted is protected from unauthorized access and interception.
Data Confidentiality: With VLESS, users can benefit from various cipher suites, including AES and ChaCha20, to ensure the confidentiality of their data. These encryption algorithms make it nearly impossible for adversaries to decipher the information being transmitted.
Obfuscation Techniques: VLESS offers obfuscation techniques that disguise network traffic, making it more challenging for adversaries to detect and block. This is particularly valuable in locations where internet censorship is prevalent, as it allows users to bypass restrictions and access blocked content.
Comparison of VLESS protocol with other protocols
When comparing VLESS with other protocols, such as Shadowsocks and WireGuard, VLESS stands out due to its robust security features and versatility.
Security: VLESS provides a higher level of security than Shadowsocks, as it incorporates encryption and obfuscation techniques that go beyond the capabilities of traditional protocols. Additionally, VLESS offers more robust encryption algorithms compared to WireGuard, making it a more secure option.
Flexibility: VLESS allows users to configure routing rules and customize their network traffic redirection, providing greater flexibility compared to Shadowsocks and WireGuard. This flexibility enables users to optimize their network performance and tailor their connection based on their specific needs.
Performance: While Shadowsocks and WireGuard are known for their fast performance, VLESS maintains a balance between security and speed. The encryption and obfuscation techniques used by VLESS ensure a secure connection without significantly impacting the performance.
In conclusion, VLESS protocol is an advanced solution that significantly boosts internet security. With its enhanced security features, robust encryption, and obfuscation techniques, VLESS provides users with a secure and reliable connection, ensuring the confidentiality and integrity of their data. Its flexibility and performance make it a competitive option compared to other protocols in the market. By adopting VLESS protocol, individuals and organizations can enhance their internet security and protect their sensitive information from potential threats.

Setting Up VLESS Protocol
Step-by-step guide to installing and configuring VLESS protocol
Setting up the VLESS protocol can seem daunting at first, but with the right guidance, it can be a straightforward process. Here is a step-by-step guide to help you install and configure VLESS:
-
Choose a suitable operating system: Determine which operating system you will be using on your server. VLESS is compatible with various operating systems, including Linux, Windows, and macOS.
-
Install V2Ray: Begin by installing V2Ray, the foundation of the VLESS protocol. You can find the installation instructions for your specific operating system in the V2Ray documentation.
-
Generate TLS certificates: To establish a secure connection, you need to generate Transport Layer Security (TLS) certificates. Use a trusted certificate authority or create self-signed certificates for testing purposes.
-
Configure the server: Modify the V2Ray configuration file to enable and configure the VLESS protocol. Specify the desired listening port, TLS certificates, and other options according to your needs.
-
Configure your client: Install a V2Ray client compatible with VLESS, such as V2RayN on Windows, V2RayNG on Android, or Clash on macOS. Enter the server details provided in the previous step, including the server address, port, and security settings.
-
Test the connection: Restart the V2Ray service on the server and launch the V2Ray client on your device. Verify that the connection is established and functioning correctly. You can test the connection by accessing websites or applications that require internet connectivity.
Recommended V2Ray clients and their setup process
To fully utilize the VLESS protocol, it is essential to use a compatible V2Ray client. Here are some recommended clients and a brief overview of their setup processes:
-
V2RayN: This Windows-based client offers a user-friendly interface and easy configuration. Download the V2RayN client from the official repository and launch it. Import the VLESS server details provided by your server administrator, and then click "Connect" to establish the VLESS connection.
-
V2RayNG: Designed for Android devices, V2RayNG provides a simple yet powerful V2Ray client. Install the V2RayNG app from the Google Play Store and open it. Enter the server details, including the server address, port, UUID, and other settings. Tap "Start" to initiate the VLESS connection.
-
Clash: Clash is a versatile V2Ray client available for macOS. Install the ClashX or Clash for Windows application on your device. Configure the client by editing the Clash configuration file and adding the VLESS server information. Launch the Clash client to connect to the VLESS server.
By following these steps and using recommended V2Ray clients, you can easily set up and enjoy the secure and reliable VLESS protocol. Ensure that you use reputable sources and follow official documentation to stay up-to-date with any changes or updates to the protocol.

Encryption and Security Features
Cipher options for VLESS protocol
The VLESS protocol offers a range of cipher options to enhance the security of your internet connections. Cipher options determine the encryption algorithm used to protect your data. Here are some commonly used cipher options for VLESS:
-
AES-128-GCM: This cipher option uses the Advanced Encryption Standard (AES) with a key size of 128 bits. It provides secure and efficient encryption, ensuring that your data remains confidential and integrity is maintained.
-
AES-256-GCM: Similar to AES-128-GCM, this cipher option employs AES with a larger key size of 256 bits. It offers even stronger encryption, making it suitable for situations where maximum security is required.
-
Chacha20-Poly1305: This cipher option combines the ChaCha20 stream cipher and the Poly1305 message authentication code. It is known for its high-speed performance and resistance against security vulnerabilities.
By selecting an appropriate cipher option, you can customize the level of encryption according to your specific security needs.
TLS encryption and certificate configuration for enhanced security
Transport Layer Security (TLS) encryption is a crucial component of the VLESS protocol, providing secure communication between the client and the server. To enhance security, it is essential to configure TLS encryption and use valid TLS certificates.
During the VLESS setup process, you need to generate TLS certificates. These certificates validate the identity of the server and encrypt the data transmitted between the client and the server. It is recommended to obtain TLS certificates from a trusted certificate authority (CA) to ensure authenticity.
TLS certificate configuration includes selecting the appropriate cipher suites, enabling secure protocols (such as TLS 1.2 or 1.3), and setting key exchange algorithms. These configurations further strengthen the security of the VLESS protocol.
By properly configuring TLS encryption and using valid TLS certificates, you can significantly boost the security of your internet connections and protect your sensitive data from unauthorized access.
Remember to always prioritize security and stay up-to-date with the latest encryption advancements to maintain a robust and secure network.
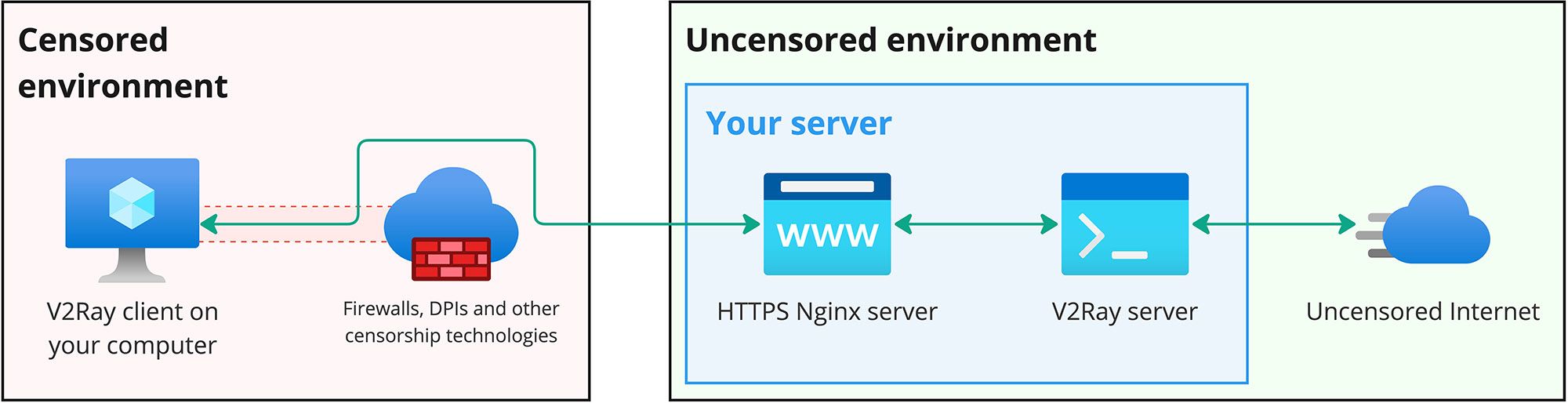
Obfuscation and Traffic Masking
Techniques to Bypass Censorship and Hide VLESS Traffic
To enhance internet security and bypass censorship restrictions, the V2Ray VLESS protocol provides several techniques for obfuscating and masking network traffic. These techniques allow users to hide their VLESS traffic, making it more difficult for authorities or organizations to detect and block it.
One technique is the use of Transport Layer Security (TLS) obfuscation. TLS obfuscation disguises VLESS traffic as regular HTTPS traffic, making it indistinguishable from normal web browsing activity. By encrypting VLESS data within a TLS tunnel, it becomes challenging for firewalls or deep packet inspection (DPI) systems to identify and block the protocol.
Another effective method is domain fronting. This technique leverages popular and widely trusted domains, such as CDN providers or social media platforms, to camouflage VLESS traffic. The traffic is routed through these domains, making it appear like legitimate traffic to the blocking systems. By utilizing domain fronting, users can bypass censorship measures and access VLESS services without arousing suspicion.
Using Domain Fronting and Camouflage Methods
In addition to domain fronting, V2Ray VLESS also supports camouflage methods to further disguise network traffic. Camouflage techniques involve altering the characteristics of VLESS traffic to resemble different protocols, such as HTTP or DNS.
By mimicking the traffic patterns and signatures of different protocols, VLESS traffic becomes harder to differentiate from regular internet activity. This makes it more challenging for authorities and network administrators to detect and block VLESS connections.
By employing these obfuscation and traffic masking techniques, the V2Ray VLESS protocol enhances internet security and privacy. Users can access restricted or censored content while maintaining anonymity and staying under the radar of censorship mechanisms.
It is worth noting that while these techniques provide a layer of protection, they are not foolproof. Governments and organizations are continuously improving their censorship and blocking methods. To ensure continued access to VLESS services, it is crucial to stay informed about new obfuscation techniques and keep the V2Ray VLESS application up-to-date.
Overall, the obfuscation and traffic masking features of the V2Ray VLESS protocol offer users a valuable tool to bypass censorship and strengthen internet security. By implementing these techniques, individuals can enjoy unrestricted access to information while safeguarding their online activities.







