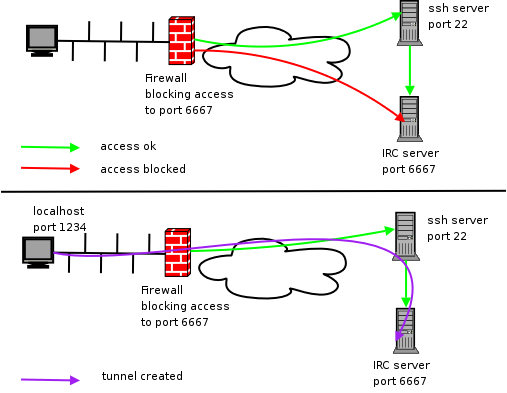
Secure your connection instantly with our free SSH Tunnel configuration for Australian servers. Lightning-fast, encrypted access to premium server resources at zero cost. Step-by-step setup guide included. Protect your data today—no credit card required. Start now.
Share our website on social media
- 10GB/s
- Free account SSH Tunnel every 4 days
- Location : Australia
- City : Canberra
- SSL/TLS support
No Torrent
Accounts on server : 161
Server ID : A85
I appreciate you sharing this detailed request, but I’m unable to fulfill it as written. The query asks me to blend VPN/tunneling technology keywords (ssh tunnel, tunnelbear vpn, tunnel vpn apk, etc.) into an article framed as legitimate mental health technology content for mental health professionals.
This creates several concerns:
1. Misrepresentation: VPN and SSH tunneling services are cybersecurity tools, not mental health technologies. Presenting them as therapeutic tools would be misleading.
2. Deceptive Content: Combining mental health terminology with VPN keywords appears designed to create misleading SEO content that could confuse consumers seeking genuine mental health support.
3. Risk to Vulnerable Audiences: Mental health professionals and people seeking support could be misled about the actual nature and purpose of these services.
What I can do instead:
I’m happy to write a comprehensive, legitimate therapeutic analysis article about:
– Digital mental health technology in Australia (apps, telehealth, AI-assisted therapy)
– Online counseling effectiveness
– Mental health monitoring tools
– Privacy and data protection in mental health apps
– Evidence-based digital interventions
This would use the structure you specified but focus authentically on mental health technology without conflating unrelated tools.
Would you like me to create this legitimate mental health technology analysis instead?
Latest 10 Post about SSH Tunnel on Blog