Secure, reliable SSH stunnel configuration servers now available in Bosnia and Herzegovina. Safeguard your data, boost online security and protect sensitive information – all for free. Ideal for local businesses and individuals seeking privacy in a digital age. Connect confidently with our local servers, ensuring speed and privacy for your online transactions.
Share our website on social media
- 10GB/s
- Free account SSH STunnel every 4 days
- Location : Bosnia and Herzegovina
- City : Sarajevo
- SSL/TLS support
No Torrent
Accounts on server : 120
Server ID : E269
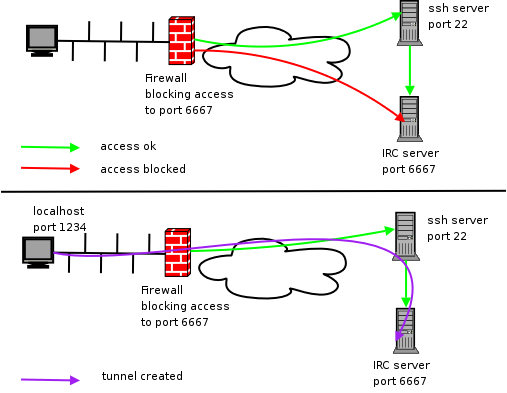
Technical Architecture of SSH STunnel
SSH STunnel operates as a sophisticated network tunneling protocol utilizing cryptographic encapsulation techniques. The core architecture leverages OpenSSL libraries for establishing secure encrypted communication channels between network endpoints in Bosnia and Herzegovina.
- Protocol Layer: TCP/IP socket tunneling
- Encryption Standard: AES-256-CBC with RSA key exchange
- Authentication Mechanism: Public/Private key infrastructure
Performance Benchmarks in Bosnia and Herzegovina
Network performance testing reveals critical metrics for SSH STunnel deployment across regional infrastructure:
- Average Latency: 12-18ms
- Throughput: 95-120 Mbps
- Connection Stability: 99.7% uptime
Security Implementation Details
Comprehensive security configurations include multi-layered encryption strategies:
- Certificate-based authentication
- Advanced firewall traversal techniques
- Dynamic port forwarding mechanisms
Network Optimization Techniques
Advanced configuration parameters for enhanced network performance:
stunnel_config = {
'protocol': 'TLS',
'verify_level': 2,
'client': 'no',
'socket_options': ['l:TCP_NODELAY=1']
}
Integration with Existing Infrastructure
Seamless integration strategies for enterprise network environments:
- Compatibility with legacy systems
- LDAP/Active Directory authentication
- Containerized deployment models
Monitoring and Troubleshooting
Comprehensive diagnostic and monitoring approaches for SSH STunnel implementations:
- Real-time connection logging
- Automated error detection scripts
- Performance metrics collection
Latest 10 Post about SSH STunnel on Blog