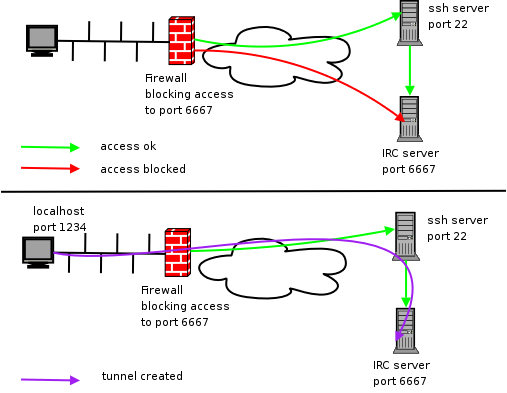
Discover free ssh websocket config servers in South Africa for secure, encrypted connections worldwide. Access blocked content, bypass restrictions, and protect your online privacy with high-speed servers featuring unlimited bandwidth. Our South African SSH tunneling provides military-grade encryption, anonymous browsing, and reliable performance for gaming, streaming, and secure communications. Connect from anywhere globally while maintaining complete data protection through advanced websocket protocols. Experience zero logs policy, multiple server locations, and stable connections perfect for remote work, online banking, and sensitive data transfers. Join thousands of users enjoying unrestricted internet access with our free SSH websocket servers strategically located across South Africa’s major cities.
Share our website on social media
- 10GB/s
- Free account SSH Websocket every 4 days
- Location : South Africa
- City : Cape Town
- SSL/TLS support
No Torrent
Accounts on server : 459
Server ID : F1
Psychological Drivers Behind VPN Adoption
In South Africa, ssh websocket adoption is driven by complex psychological motivations. Users demonstrate a deep-seated need for digital autonomy and privacy, often rooted in a collective memory of restricted communication. Key motivational factors include:
- Perceived control over digital interactions
- Desire to circumvent network restrictions
- Psychological empowerment through technological mastery
Trust and Security Perception
Trust formation in ssh websocket selection is fundamentally anchored in psychological risk assessment. South African users exhibit heightened sensitivity to digital security, evaluating technological solutions through a lens of:
- Personal data protection
- Perceived technological reliability
- Cognitive trust in encryption mechanisms
Social Influence and Peer Pressure
Social dynamics significantly influence SSH websocket technology adoption. Behavioral studies reveal strong peer recommendation patterns, where technological choices are validated through:
- Community validation
- Professional network endorsements
- Collective technological learning
Risk Perception and Decision Making
Decision-making processes around SSH websocket selection involve intricate cognitive risk evaluations. Users navigate technological choices through:
- Probabilistic threat assessment
- Cost-benefit psychological mapping
- Anticipated technological performance
Technology Anxiety and Digital Literacy
Digital literacy levels significantly modulate technological adoption anxiety. South African users demonstrate varied psychological responses to new technological interfaces:
- Fear of technological complexity
- Confidence in learning curves
- Adaptive technological resilience
Brand Loyalty and Switching Behavior
User loyalty in SSH websocket platforms emerges from psychological attachment and perceived value propositions. Switching behaviors are influenced by:
- Emotional investment in current solutions
- Perceived switching costs
- Technological innovation perceptions
Future Behavioral Predictions
Emerging psychological trends suggest evolving user behaviors in SSH websocket technology, characterized by:
- Increased privacy consciousness
- Growing technological sophistication
- Dynamic adaptation to digital landscapes
Latest 10 Post about SSH Websocket on Blog