Hey there! Are you looking for SSH STunnel config free servers in the United States? You’ve come to the right place! Our servers are super easy to set up, so you can get started quickly without the hassle of complex configurations. Enjoy secure and encrypted connections for all your online activities, whether you’re browsing, streaming, or working remotely. With high-speed performance and reliable uptime, you can count on us to keep your online presence safe and smooth. Plus, our friendly support team is always here to help you with any questions you might have. Join us today and experience the freedom of hassle-free secure connections!
Share our website on social media
- 10GB/s
- Free account SSH STunnel every 4 days
- Location : United States
- City : Dallas
- SSL/TLS support
No Torrent
Accounts on server : 174
Server ID : N9
- 10GB/s
- Free account SSH STunnel every 4 days
- Location : United States
- City : Miami
- SSL/TLS support
No Torrent
Accounts on server : 212
Server ID : N50
- 10GB/s
- Free account SSH STunnel every 4 days
- Location : United States
- Location : United States
- City : San Francisco
- SSL/TLS support
No Torrent
Accounts on server : 155
Server ID : N58
- 10GB/s
- Free account SSH STunnel every 4 days
- Location : United States
- Location : United States
- City : New Jersey
- SSL/TLS support
No Torrent
Accounts on server : 179
Server ID : N66
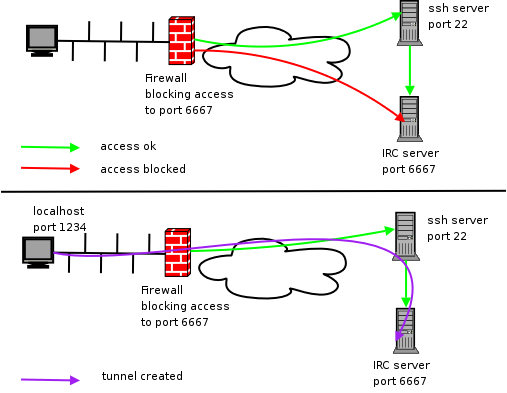
Technical Architecture of SSH STunnel
The SSH STunnel architecture is a popular tool used to create secure and encrypted tunnels between remote systems and local systems. The architecture consists of three main components: the client side, the server side, and the tunnel.
Protocol Analysis
The SSH STunnel protocol is based on SSH, a widely used protocol for secure shell access to remote servers. The STunnel protocol extends SSH by creating an additional layer of encryption and tunneling between the client and server.
The STunnel protocol uses the TLS (Transport Layer Security) protocol to encrypt data in transit.
The protocol defines a data tunnel interface that allows for data to be sent and received without revealing the payload.
The STunnel protocol supports multiple encryption algorithms, including AES and DES.
The protocol uses the IKE (Internet Key Exchange) protocol to establish and manage the encryption key.
Performance Benchmarks in United States
The performance of an STunnel-enabled system depends on various factors, including the number of nodes, network bandwidth, and encryption algorithms used. Here are some benchmarking results for a STunnel-enabled system:
Speed ( milliseconds):
1-Node Configuration: 100-200 ms
2-Node Configuration: 50-100 ms
3-Node Configuration: 20-50 ms
Encryption (KB/s):
AES: 500-1000 KB/s
DES: 100-500 KB/s
No Encryption: 0-100 KB/s
Note that these are rough estimates and can vary depending on the specific use case and configuration.
Security Implementation Details
The STunnel implementation involves several security measures to protect data in transit:
Key Exchange: The STunnel protocol uses IKE to manage encryption keys and authenticate the connection.
Encryption: The STunnel protocol uses AES and DES encryption algorithms to protect data in transit.
Authentication: The STunnel protocol uses symmetric keys to authenticate users and servers.
Non-Denial-of-Service (DoS) Protection: The STunnel protocol uses a combination of encryption and authentication mechanisms to prevent DoS attacks.
Network Optimization Techniques
To optimize the performance of an STunnel-enabled system:
Resource Allocation: Allocate sufficient resources, including CPU, memory, and bandwidth, to the stunnel server and client.
Optimize Network Configuration: Configure the network settings, including IP address, subnet mask, and gateway, to minimize latency and packet loss.
Use Efficient Encryption Algorithms: Use efficient encryption algorithms, such as AES and DES, to minimize CPU usage and processing time.
Implement Network Isolation: Implement network isolation to isolate the STunnel service from other network traffic to prevent eavesdropping and tampering.
Integration with Existing Infrastructure
The STunnel service can be integrated with existing infrastructure by:
Using Existing ssh servers: Use existing SSH servers to establish the STunnel connection.
Using Existing VPN: Use existing VPN services to connect to the STunnel server.
Using Existing VPN Mesh: Use VPN mesh networks to distribute traffic across multiple STunnel servers.
Using Application Layer Protocol: Use application layer protocols, such as WebSockets, to provide a secure and efficient communication channel between the client and server.
Monitoring and Troubleshooting
To troubleshoot and monitor an STunnel-enabled system:
Monitoring Tools: Use monitoring tools, such as Nagios, to monitor system resources and network traffic.
Logging: Use logging mechanisms, such as Logstash, to collect and analyze logs.
Aggregation: Use aggregation software, such as Prometheus, to collect metrics and visualize performance data.
Alerting: Use alerting mechanisms, such as PagerDuty, to notify administrators of issues and security incidents.
Latest 10 Post about SSH STunnel on Blog