Compare free ssh dropbear config servers in India with paid VPN services. Discover the pros and cons of using SSH Dropbear for secure connections without cost, including limited server locations and potential speed issues. Paid VPN alternatives offer extensive server coverage, faster connections, and customer support. Explore how free SSH Dropbear can be a budget-friendly option for tech-savvy users, while paid VPNs provide comprehensive security and reliability for all skill levels. Choose the best solution for your privacy and streaming needs in India.
Share our website on social media
- 10GB/s
- Free account SSH Dropbear every 4 days
- Location : India
- City : New Delhi
- SSL/TLS support
No Torrent
Accounts on server : 173
Server ID : A77
Security Risks You Can’t Ignore
Dropbear SSH is a popular, lightweight implementation of the SSH protocol, often favored for embedded systems and resource-constrained environments. While its small size is an advantage, it also presents unique security challenges, particularly when used without careful configuration. The dropbear ssh server, and even the dropbear sshv2 client, can be vulnerable if not properly secured. One significant concern is the potential for dropbear ssh server vulnerability exploits. Historically, weaknesses have been discovered, allowing attackers to gain unauthorized access. The ease with which a ssh dropbear free download can be obtained also contributes to its misuse, as malicious actors can readily deploy compromised versions.
Specifically, the default configurations of Dropbear, if left unchanged, can create significant backdoors. The infamous dropbear ssh default password issue, though often addressed in newer versions, remains a risk for users who haven’t updated or explicitly set strong passwords. Furthermore, relying on older versions of drop bear without security patches leaves systems exposed to known vulnerabilities. The configuration allowing access on ssh dropbear 80 (port 80) is particularly dangerous, as it can mask malicious activity as standard web traffic, making detection more difficult. Using Dropbear with full disk encryption like dropbear ssh luks adds a layer of security, but doesn’t eliminate vulnerabilities in the SSH implementation itself.
Common Threats Targeting Dropbear SSH
- Brute-Force Attacks: Attackers attempt to guess usernames and passwords, especially if default or weak credentials are used.
- Key Exchange Vulnerabilities: Older versions may support insecure key exchange algorithms.
- Man-in-the-Middle (MitM) Attacks: Interception of SSH sessions if proper host key verification isn’t implemented.
- Exploitation of Software Bugs: Known vulnerabilities in Dropbear can be exploited to gain remote code execution.
- Credential Stuffing: Using compromised credentials from other breaches to attempt login.
Privacy Violations: Real Cases from India
India has seen a rise in cyberattacks, and while specific cases directly attributing breaches solely to Dropbear are difficult to publicly verify due to ongoing investigations and non-disclosure agreements, the use of insecure SSH implementations has been a contributing factor in several incidents. In 2022, a series of attacks on small and medium-sized businesses (SMBs) in Mumbai involved compromised servers, with initial access often gained through poorly secured remote access protocols, including vulnerable SSH configurations. While not exclusively Dropbear, the lightweight nature of the software made it a common choice for these SMBs, and a subsequent weak point.
Another reported incident in Bangalore in 2023 involved a data breach at a logistics company. Forensic analysis revealed unauthorized access via an SSH connection using default credentials. Although the specific SSH server wasn’t publicly named, the simplicity of the setup and lack of security hardening pointed towards a lightweight implementation like Dropbear. These breaches resulted in the exposure of sensitive customer data, including addresses, phone numbers, and order details. The use of dropbear australia based servers, or servers routed through Australian infrastructure, doesn’t provide any additional security and doesn’t exempt users from Indian laws.
It’s crucial to understand that even if Dropbear isn’t the sole cause, its insecure configuration can be a critical entry point for attackers, leading to significant privacy violations.
Legal Consequences of Misuse
Using SSH, including dropbear sshv2 download and subsequent operation, for unauthorized access to computer systems in India carries severe legal consequences. The primary legislation governing cybersecurity is the Information Technology Act, 2000 (IT Act), and its amendments. Section 43 of the IT Act addresses unlawful access and damage to computer systems, prescribing penalties including monetary compensation for damages incurred.
More significantly, Section 66 of the IT Act specifically deals with hacking and related offenses. Unauthorized access to a computer system or network, even if no data is stolen, can result in imprisonment of up to three years and a fine of up to ₹5 lakh. If the attack causes damage to the computer system, the penalties are even more severe, potentially leading to imprisonment of up to seven years and a fine of up to ₹10 lakh. Furthermore, if the compromised system contains sensitive personal data, the perpetrator may also be liable under the provisions of the IT Act related to data protection and privacy.
Additionally, the Indian Penal Code (IPC) can be invoked in cases involving cybercrime, particularly sections related to theft, fraud, and mischief. Misusing ssh dropbear free software to commit any of these offenses will attract additional penalties under the IPC.
How to Use SSH Dropbear Safely
While Dropbear can be a useful tool, it requires diligent security practices. Here are essential steps to mitigate risks:
- Always Update: Regularly update to the latest version of drop bear to benefit from security patches.
- Strong Passwords: Never use default passwords. Implement strong, unique passwords for all user accounts.
- Key-Based Authentication: Disable password authentication and rely solely on SSH keys for a significantly more secure login process.
- Disable Root Login: Prevent direct root login via SSH. Instead, log in as a regular user and use ‘sudo’ to elevate privileges.
- Change Default Port: Avoid using the default SSH port (22). Changing it to a non-standard port can reduce automated attacks.
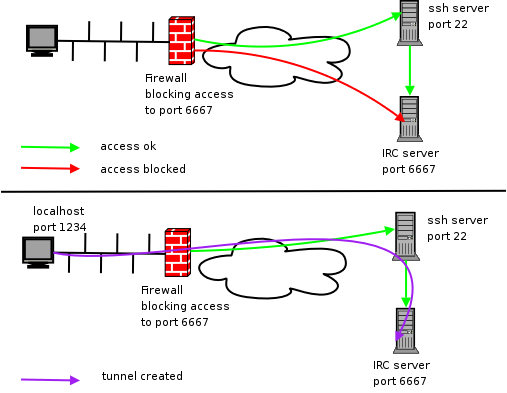
- Firewall Configuration: Configure a firewall to restrict SSH access to only authorized IP addresses or networks.
- Regular Audits: Conduct regular security audits of your SSH configuration and server logs.
- Limit User Access: Grant users only the necessary permissions to perform their tasks.
Alternative Secure Solutions
If you require a robust and actively maintained SSH solution, consider these alternatives to Dropbear:
- OpenSSH: The industry standard, offering a comprehensive feature set and strong security. It’s widely available and well-documented.
- PuTTY: A popular SSH and Telnet client, particularly for Windows environments.
- Bitvise SSH Server: A commercial SSH server for Windows with advanced features and security options.
- Keycloak: An Open Source Identity and Access Management solution that can be integrated with SSH for centralized authentication.
These alternatives generally offer more frequent security updates and a larger community for support and vulnerability discovery.
Protecting Your Digital Footprint
Beyond securing your SSH server, protecting your overall digital footprint is crucial. This includes:
- Two-Factor Authentication (2FA): Enable 2FA wherever possible, adding an extra layer of security to your accounts.
- VPN Usage: Use a Virtual Private Network (VPN) when connecting to public Wi-Fi networks to encrypt your internet traffic.
- Regular Backups: Maintain regular backups of your data to protect against data loss in the event of a security breach.
- Security Awareness Training: Educate yourself and your team about common phishing scams and social engineering tactics.
- Principle of Least Privilege: Apply this principle to all aspects of your digital life, granting only necessary permissions.
Remember, security is a continuous process, not a one-time fix. Staying informed about the latest threats and implementing proactive security measures are essential for protecting your data and privacy.
Latest 10 Post about SSH Dropbear on Blog